When you hide a message inside of another message, it’s called steganography. While you might not have known it’s name, this technique has a long and colourful history and it is still used today by cybercriminals.

Why do all incident response communications from customers feel the same? Why do they all miss the mark? How hard is it to do better?
Shellshock is a surprising bug. Hidden for decades, what do you need to know to help your organization respond?

Cloud computing is more than just fast self-service of virtual infrastructure. Developers and admins are looking for ways to provision and manage at scale.

If you strip away a lot of security terminology, it’s really about understanding what’s going on. If you want slap a fancy term back on, let’s call that “situational awareness”
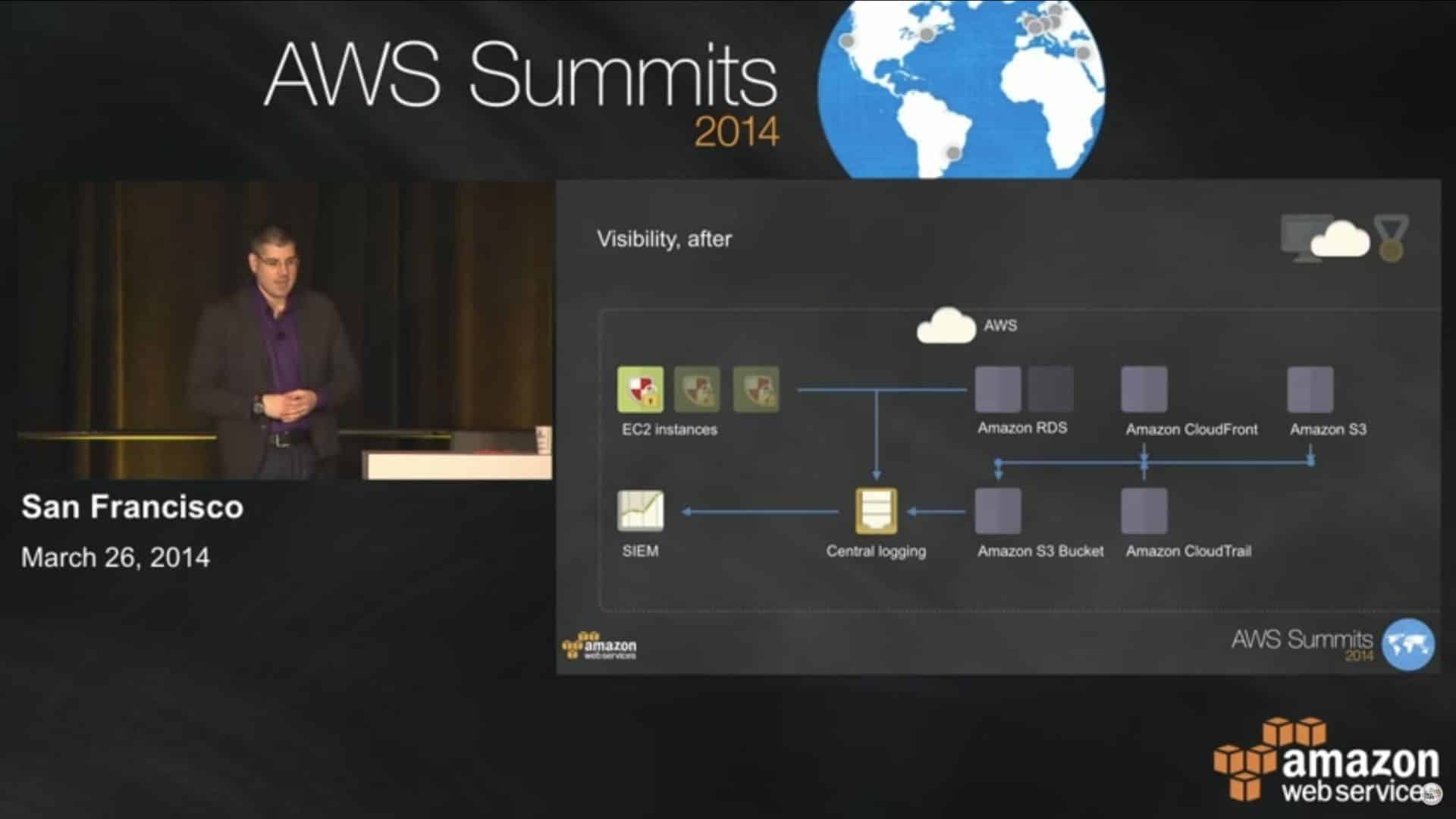
As AWS opened their summit series for 2014, 5000+ people packed into the Moscone Center. There was a ton of energy in the air and I got to talk about updating security operations for the cloud.

What does a modern security practice look like in the cloud? How do each of the area change?

Forensics is an area that’s often lacking in corporate environments. Few people have time to truly dig into an incident after it’s been resolved. Can we make forensics easier in the cloud?

Network security monitoring is changing dramatically in the cloud as more and more responsibilities are shifted to the Cloud Service Provider. How should your team adjust?