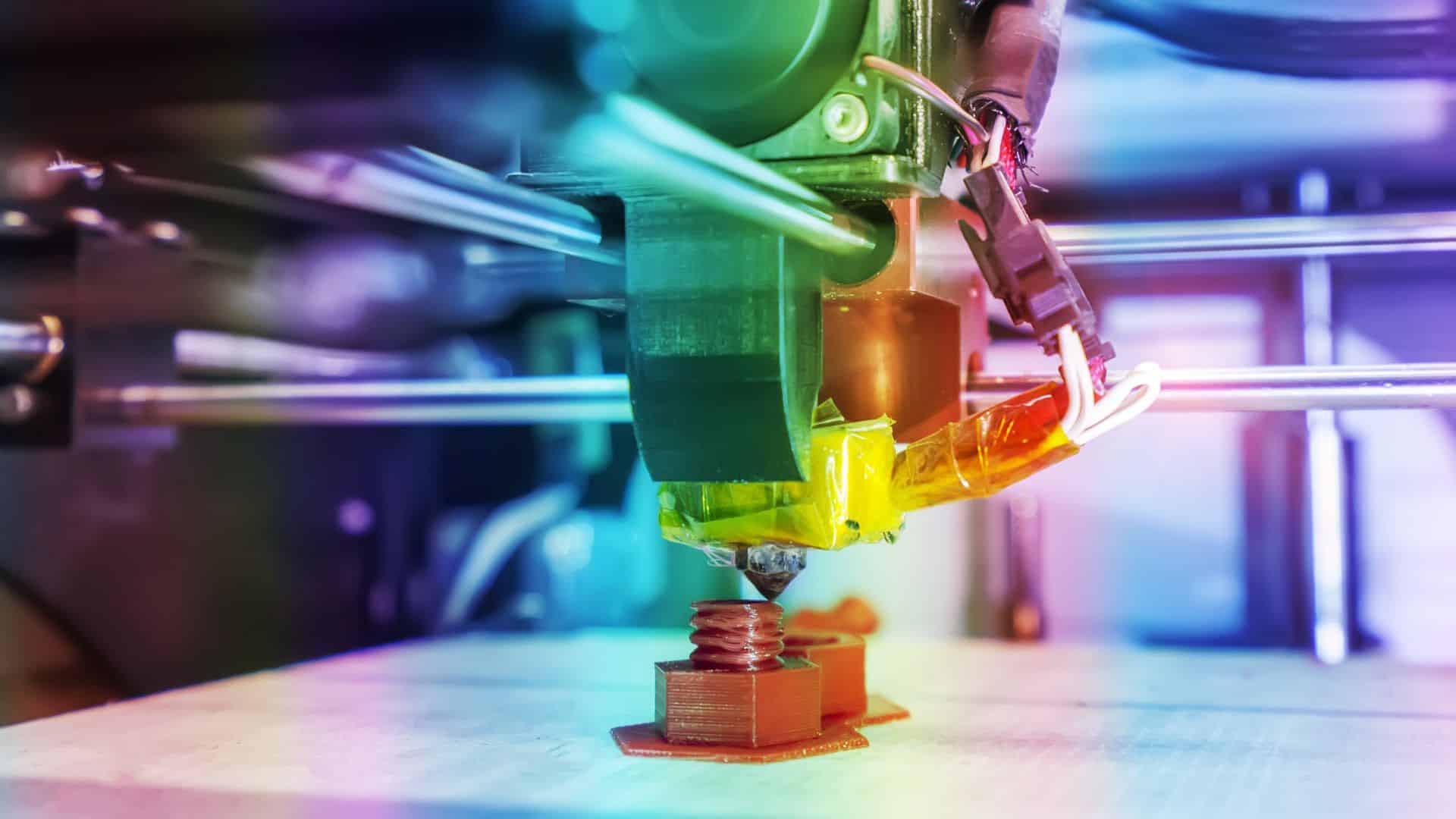
3d printing holds a mountain of promise. While the technology is taking longer than generally expected to make an impact, the areas where it is having an impact are significant. While copyright and outdated thinking get in the way of this technology?
We’re creating more and more data but despite advancements in data processing, we’re still lacking easy to use tools to understand what’s happening around us. What can we do to fix this?
No one wins all the time. Don’t seek out failure but we shouldn’t be afraid of sharing our failures so that others may learn.

Is that video real? Are you sure? A new technique makes it easier than ever to create passable fake videos of prominent people. You cannot trust your eyes anymore.
A lot of the issues facing our communities and sub communities today (deep fakes, encryption, privacy, DevOps, etc.) need active discussions. By their very nature, you can’t really have discussions at scale…right?
Unchecked assumptions are a major risk in any field…but in cybersecurity they take on a whole new level

Is your phone trying to trick you into never putting it down? Smartphone addiction has become such a massive problem that the two major operating systems—Apple and Android—now include features designed to help you use your device less. Is this wh...
Where–physically–do you work? Does it matter?
It’s all too easy to burnout in IT in general…more so in security. Why? What’s the cost?
Some perceptions override the logic behind risk decisions. How do you fight through to make a sound decision?
The popular perception of A.I. does not line up with it’s current capabilities. A look at what’s real and what’s not.
Design has a massive impact on user behaviour. Sadly, it’s often ignored when it comes to security and privacy.