All posts on markn.ca covering cloud, security, privacy, and technology.
A friend highlighted a real issue: there isn’t enough material about basic cybersecurity that’s easily relatable.
Connecting with others is critical but it can also pose a risk. It’s important not to “leak” information needlessly. This is a practice know as operational security. It’s critically important…and often ignored.
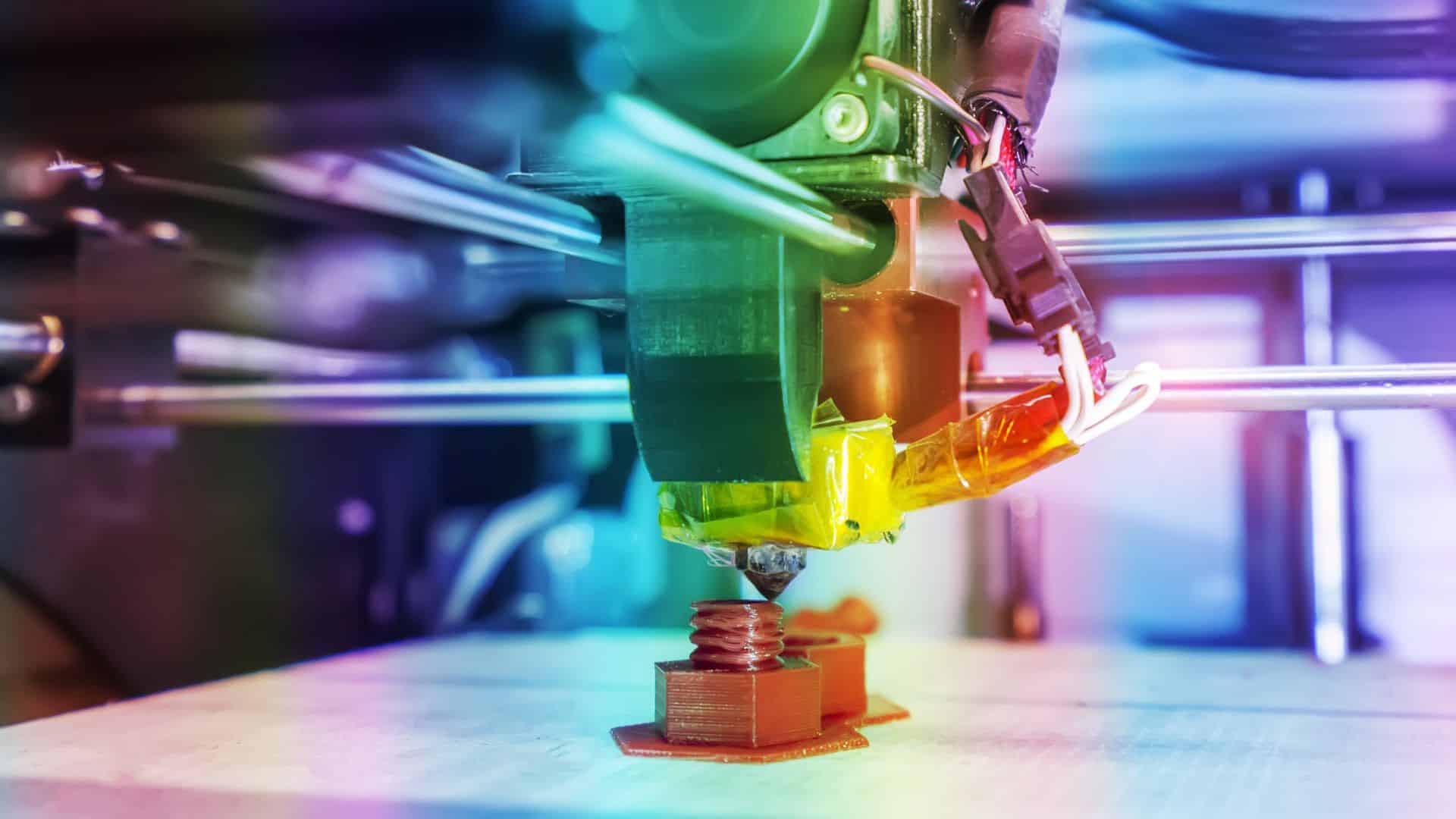
3d printing holds a mountain of promise. While the technology is taking longer than generally expected to make an impact, the areas where it is having an impact are significant. While copyright and outdated thinking get in the way of this technology?
We’re creating more and more data but despite advancements in data processing, we’re still lacking easy to use tools to understand what’s happening around us. What can we do to fix this?
No one wins all the time. Don’t seek out failure but we shouldn’t be afraid of sharing our failures so that others may learn.
Security is there to ensure that the systems you build work only as intended. Part of that is realizing the potential for abuse and ensuring that the system and users can continue to work safely…there’s a LOT of work to do.
A lot of the issues facing our communities and sub communities today (deep fakes, encryption, privacy, DevOps, etc.) need active discussions. By their very nature, you can’t really have discussions at scale…right?

Is that video real? Are you sure? A new technique makes it easier than ever to create passable fake videos of prominent people. You cannot trust your eyes anymore.
Getting your first cybersecurity role can be difficult. Is part of the problem how organizations are hiring talent?
Passwords are a horrible way to verifying identities but they are the best thing we currently have that works at scale. Adding a 2nd factor to that verification significantly increases the security of the system. But how can you add that factor witho...
You cannot stand at “Red Alert” 24/7 but that’s exactly what we do in cybersecurity…often without realizing it. What impact does that have an our approach? Our attitude? Our mental health?
Unchecked assumptions are a major risk in any field…but in cybersecurity they take on a whole new level